How Replication transfer events from Master to Slave in MySQL
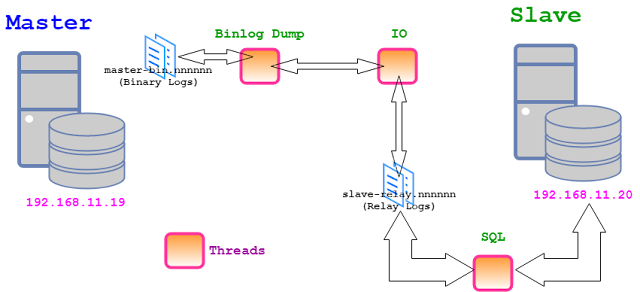
In MySQL the events (write operations) are transferred from master to slave with the help of threads. Thread Name Runs On Binlog Dump Master IO Slave SQL Slave and in the following chronological order. The slave connects to the master (as a client) using the credentials that were given during setup. This credentials are set by executing CHANGE MASTER TO at slave side. It might be possible that MySQL is storing the credentials in a plain form. Hence it is advisable to create a separate user in Master with privileges that grant it the power of serving the purpose of replication only. IO thread from the slave asks for new events in the master if any. Binlog Dump thread from master checks this and send contents to IO thread if new events are do present. IO thread then writes the new events to the relay logs on slave. SQL thread on the slave then reads these events from relay logs and apply them to the database. This is how


